Enhanced cyber security posture
11 March 2022

This poses three critical issues for organisations:
| 1. HOW DO YOU ADOPT “ENHANCED CYBER SECURITY POSTURE”? |
|---|
The Australian Cyber Security Centre’s (ACSC) most recent alert2 points to an increasing threat of deployment of destructive malware, triggered by events in Ukraine.
|
| 2. DO YOU VOLUNTARILY COMPLY WITH PENDING REGULATIONS? |
Organisations are now being asked to voluntarily comply with proposed amendments currently before Parliament to introduce a requirement to implement a risk management program and enhanced risk measures for systems of national significance.
|
| 3. ARE YOU PREPARED TO RESPOND AND ACCELERATE RECOVERY? |
Even organisations who are confident about their cyber controls will need to review their preparedness for cyber incidents.
|
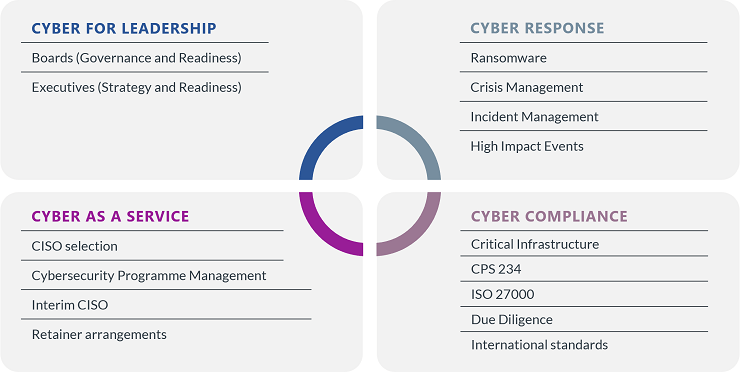
Ashurst’s combined Legal and Risk Advisory expertise in cyber security is accessed by large listed companies, global organisations, leadership teams and Boards so they can improve the governance, compliance, risk management and crisis response to cyber security. We have deep expertise in issues such as ransomware, data breaches, geo-politically motivated attacks, regulatory investigations and industry-wide preparedness.
Our recent experience includes supporting clients throughout data breach and ransomware incidents, including advising on crisis management operations, engagement with Threat Actors, the legal and operational issues with ransomware payments, forensic investigations, regulatory notifications, governance and assurance of cyber response and recovery, cyber insurance and managing third party advisors and service providers. We also regularly advise Boards and leadership teams on cyber reporting and metrics, cyber governance, team structure and operating models and cyber due diligence for acquisitions.
Ashurst Risk Advisory Pty Ltd (ABN 74 996 309 133) provide services under the Ashurst Consulting brand. Ashurst Consulting services do not constitute legal services or legal advice, and are not provided by Australian legal practitioners. The laws and regulations which govern the provision of legal services in the relevant jurisdiction do not apply to the provision of non-legal services.
For more information about the Ashurst Group and the services offered, please visit www.ashurst.com.
Liability limited by a scheme approved under Professional Standards Legislation (Ashurst Risk Advisory only).
1. See CISC Action Alert here
2. See “ACSC - 2022-02: Australian organisations should urgently adopt an enhanced cyber security posture” here
The information provided is not intended to be a comprehensive review of all developments in the law and practice, or to cover all aspects of those referred to.
Readers should take legal advice before applying it to specific issues or transactions.





Sign-up to select your areas of interest
Sign-up